NIST CONTROLS
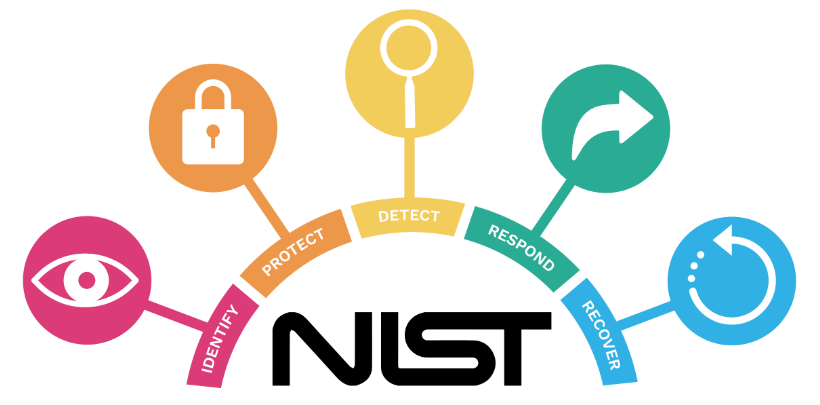
What is NIST Controls?
The National Institute of Standards and Technology (NIST) Cybersecurity Framework serves as a valuable roadmap for organizations to improve their cybersecurity posture. Within it lies a crucial component: NIST Controls. These over 900 unique controls, organized into 18 larger control families, provide a comprehensive set of best practices for mitigating cybersecurity risks.
Why does your Organization require NIST Controls?
- Reduced Risk of Attacks: Implementing NIST controls helps identify and address vulnerabilities, minimizing the attack surface and making it harder for attackers to gain access to your systems.
- Improved Threat Detection and Response: The controls outline best practices for threat detection and response, allowing you to identify and react to security incidents quickly and effectively.
- Proactive Approach to Security: NIST controls encourage a proactive approach to cybersecurity, focusing on preventing incidents rather than just reacting to them.
- Enhanced Stakeholder Confidence: Implementing NIST controls demonstrates your commitment to cybersecurity, fostering trust with clients, partners, and investors.
- Competitive Advantage: Strong security is increasingly important in today’s data-driven world, and NIST compliance can set you apart from competitors.
- Improved Relationships: Strong security practices built on a recognized framework lead to better collaboration and trust with external stakeholders.


Why does your Organization require NIST Controls?
- Reduced Risk of Attacks: Implementing NIST controls helps identify and address vulnerabilities, minimizing the attack surface and making it harder for attackers to gain access to your systems.
- Improved Threat Detection and Response: The controls outline best practices for threat detection and response, allowing you to identify and react to security incidents quickly and effectively.
- Proactive Approach to Security: NIST controls encourage a proactive approach to cybersecurity, focusing on preventing incidents rather than just reacting to them.
- Enhanced Stakeholder Confidence: Implementing NIST controls demonstrates your commitment to cybersecurity, fostering trust with clients, partners, and investors.
- Competitive Advantage: Strong security is increasingly important in today’s data-driven world, and NIST compliance can set you apart from competitors.
- Improved Relationships: Strong security practices built on a recognized framework lead to better collaboration and trust with external stakeholders.
Our Approach
1. Identifying the Relevant Controls:
- Assisting in Choosing the Appropriate NIST Publication: Different publications, like SP 800-53 ("Security and Privacy Controls for Federal Information Systems and Organizations") or SP 800-161 ("Supply Chain Risk Management Practices"), contain diverse control sets.
- Assisting in Understanding the Control Families: Each publication categorizes controls into families based on security objectives (e.g., access control, data protection, risk assessment), and Aligning the appropriate control family with your needs.
- Prioritizing Controls: Conducting a risk assessment to identify high-impact threats and select controls that effectively address them.
2. Implementing and Documenting the Controls:
- Selecting Implementation Methods: Choosing tools, technologies, and processes to enact the chosen controls (e.g., access control software, data encryption tools).
- Configuring Systems and Devices: Applying the chosen methods to secure systems and data according to control specifications.
- Documenting Implementation Details: Maintaining clear records of deployed controls, configurations, and responsible personnel.
3. Testing and Monitoring Effectiveness:
- Validating Control Effectiveness: Conducting penetration testing, vulnerability scans, and internal audits to ensure controls function as intended.
- Monitoring ongoing Activity: Tracking system logs, access attempts, and security events to detect potential breaches and control bypasses.
- Continuously Measuring Progress: Using metrics and reports to evaluate control performance and identify areas for improvement.
4. Maintaining and Updating Controls:
- Addressing Vulnerabilities: Applying security patches, updating configurations, and remediating identified weaknesses regularly.
- Responding to Evolving Threats: Adapting controls and strategies based on new threat intelligence and revised NIST publications.
- Refining and Optimizing: Conducting periodic reviews to security controls and make necessary adjustments.