INFOSEC CONTINUAL IMPROVEMENT AND SUPPORT

What is Infosec Continual Improvement and Support ?
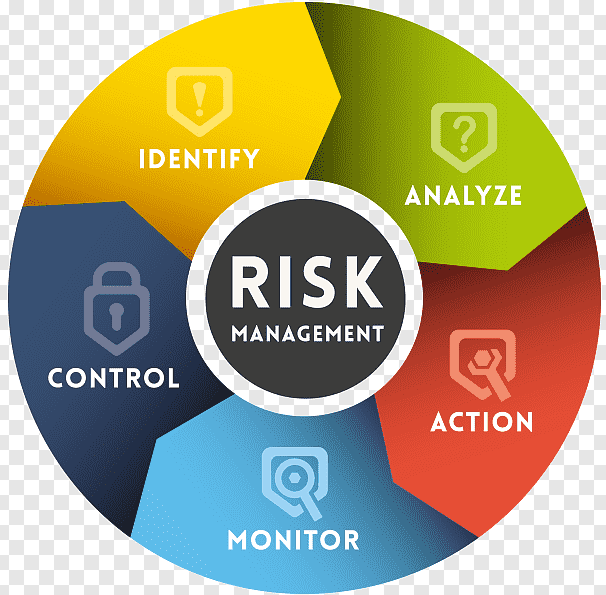
Infosec Continual Improvement and Support is a crucial approach to proactively enhance your organization’s information security posture. It involves a cyclical process of identifying vulnerabilities, analyzing risks, implementing controls, monitoring effectiveness, and making adjustments as needed. This ensures your security practices stay relevant and adaptive in the face of ever-evolving cyber threats.
Benefits of Infosec Continual Improvement and Support ?
- Enhanced Security Posture: Reduces the risk of successful cyberattacks and data breaches.
- Compliance with Regulations: Helps organizations comply with relevant data privacy and security regulations.
- Cost Savings: Proactive mitigation prevents costly incident response and recovery efforts.
- Improved Business Continuity: Minimizes disruptions caused by security incidents.
- Increased Transparency and Trust: Demonstrates commitment to responsible data handling and builds trust with stakeholders.


Benefits Of Infosec Continual Improvement and Support ?
- Enhanced Security Posture: Reduces the risk of successful cyberattacks and data breaches.
- Compliance with Regulations: Helps organizations comply with relevant data privacy and security regulations.
- Cost Savings: Proactive mitigation prevents costly incident response and recovery efforts.
- Improved Business Continuity: Minimizes disruptions caused by security incidents.
- Increased Transparency and Trust: Demonstrates commitment to responsible data handling and builds trust with stakeholders.
Our Approach
1. Continuous Monitoring and Assessment:
Regularly identify and assess risks and vulnerabilities through activities like:
- Vulnerability Scanning: Identify known weaknesses in your systems and applications.
- Penetration Testing: Simulate real-world attacks to uncover potential security breaches.
- Security Incident and Event Monitoring (SIEM): Analyze logs and security events for suspicious activity.
- Security Awareness Training: Evaluate employee understanding of security risks and best practices.
2. Prioritization and Remediation:
- Analyze identified risks based on their severity, impact, and likelihood of exploit.
- Prioritize remediation efforts based on the criticality of assets and potential consequences of successful attacks.
- Implement appropriate mitigation measures like patching vulnerabilities, updating software, or improving access controls.
3. Incident Response and Recovery:
- Establish a defined incident response plan to effectively handle security incidents.
- Practice and test your incident response plan regularly to ensure preparedness.
- Develop and maintain disaster recovery plans to minimize downtime and data loss in case of incidents.
4. Policy and Procedure Updates:
- Regularly review and update your security policies and procedures to reflect evolving threats and best practices.
- Ensure policies are easily accessible and understood by all employees.
- Conduct regular training and awareness programs to reinforce policy adherence.
5. Ongoing Learning and Improvement:
- Stay informed about emerging threats and vulnerabilities through threat intelligence feeds and industry publications.
- Attend security conferences and workshops to learn about new technologies and best practices.
- Encourage continuous learning and knowledge sharing within your organization.
6. Measurement and Reporting:
- Define Key Performance Indicators (KPIs) to track the effectiveness of your Infosec C&S program.
- Regularly measure progress towards achieving your security goals.
- Communicate results and any identified weaknesses to leadership and stakeholders.