SIG - STANDARDIZED INFORMATIION GATHERING
What is SIG – Standardized Information Gathering?
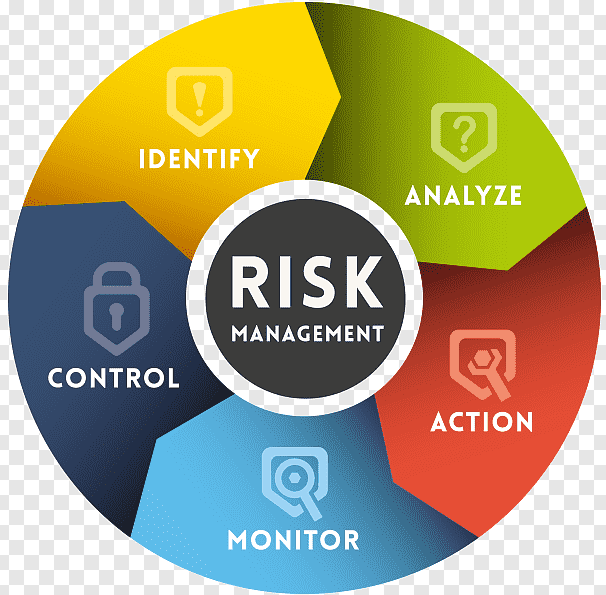
SIG stands for Standardized Information Gathering. It refers to a repository of questions designed to assess the security and privacy practices of third-party vendors.
Benefits of SIG – Standardized Information Gathering?
- Reduced Redundancy: Eliminates the need for custom questionnaires for each vendor, saving time and resources for both parties.
- Consistent Approach: Ensures all vendors are assessed against the same set of relevant questions, creating a level playing field and simplifying comparisons.
- Automation Potential: Allows leveraging software tools to automate questionnaire distribution, response collection, and analysis, further streamlining the process.
- Comprehensive Coverage: SIG questionnaires address a wide range of risk domains, including information security, data privacy, operational resilience, and financial stability.
- Aligned with Regulations: Maps to various regulations and frameworks, simplifying compliance efforts and demonstrating due diligence.
- Deeper Insights: SIG Core offers a more in-depth assessment compared to Lite, providing a clearer picture of vendor risk profiles.


Benefits of SIG – Standardized Information Gathering?
- Reduced Redundancy: Eliminates the need for custom questionnaires for each vendor, saving time and resources for both parties.
- Consistent Approach: Ensures all vendors are assessed against the same set of relevant questions, creating a level playing field and simplifying comparisons.
- Automation Potential: Allows leveraging software tools to automate questionnaire distribution, response collection, and analysis, further streamlining the process.
- Comprehensive Coverage: SIG questionnaires address a wide range of risk domains, including information security, data privacy, operational resilience, and financial stability.
- Aligned with Regulations: Maps to various regulations and frameworks, simplifying compliance efforts and demonstrating due diligence.
- Deeper Insights: SIG Core offers a more in-depth assessment compared to Lite, providing a clearer picture of vendor risk profiles.
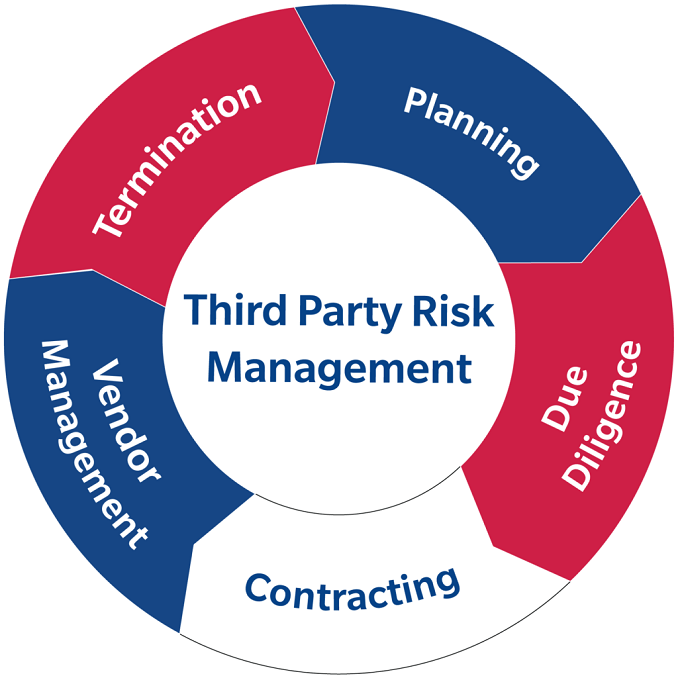
Our Approach
1. Planning and Scoping:
- Defining Requirements: Identifying the specific risks and objectives of the assessment. This could involve regulatory compliance, data security concerns, or operational resilience risks.
- Selecting Vendors: Determining which third-party vendors require assessment based on their criticality and potential risk exposure.
2. Questionnaire Distribution and Completion:
- Customize Questionnaire: Adapting the chosen SIG questionnaire to fit your specific risk areas and regulatory requirements.
- Distribute Questionnaire: Sending the questionnaire to the selected vendors with clear instructions and deadlines for completion.
- Monitoring and Tracking: Ensuring timely completion by vendors and addressing any questions or clarifications they might have.
3. Information Review and Analysis:
- Collecting Responses: Gathering completed questionnaires from vendors and consolidate them into a central platform for analysis.
- Evaluating Responses: Assessing the completeness and accuracy of provided information, looking for areas of potential risk or inconsistencies.
- Performing Gap Analysis: Comparing vendor responses against your desired risk profiles and identify any gaps in controls or compliance processes.
4. Risk Scoring and Mitigation Strategies:
- Developing Risk Scorecard: Assigning risk scores to vendors based on their responses and identified gaps in controls and compliance.
- Prioritizing Vendors: Focusing on subsequent steps on high-risk vendors that warrant deeper investigation or remediation actions.
- Requesting Additional Information: Engaging with high-risk vendors to clarify concerns, request supporting documentation, or conduct follow-up interviews.
5. Final Assessment and Remediation:
- Developing Action Plan: Defining specific actions for high-risk vendors, including additional due diligence, control enhancements, or contract renegotiations.
- Monitoring and Tracking Action Items: Overseeing the implementation of agreed-upon remediation actions by vendors and track progress towards improved risk posture.
- Maintain Ongoing Dialogue: Regularly engaging with vendors to ensure sustained adherence to security and compliance standards.