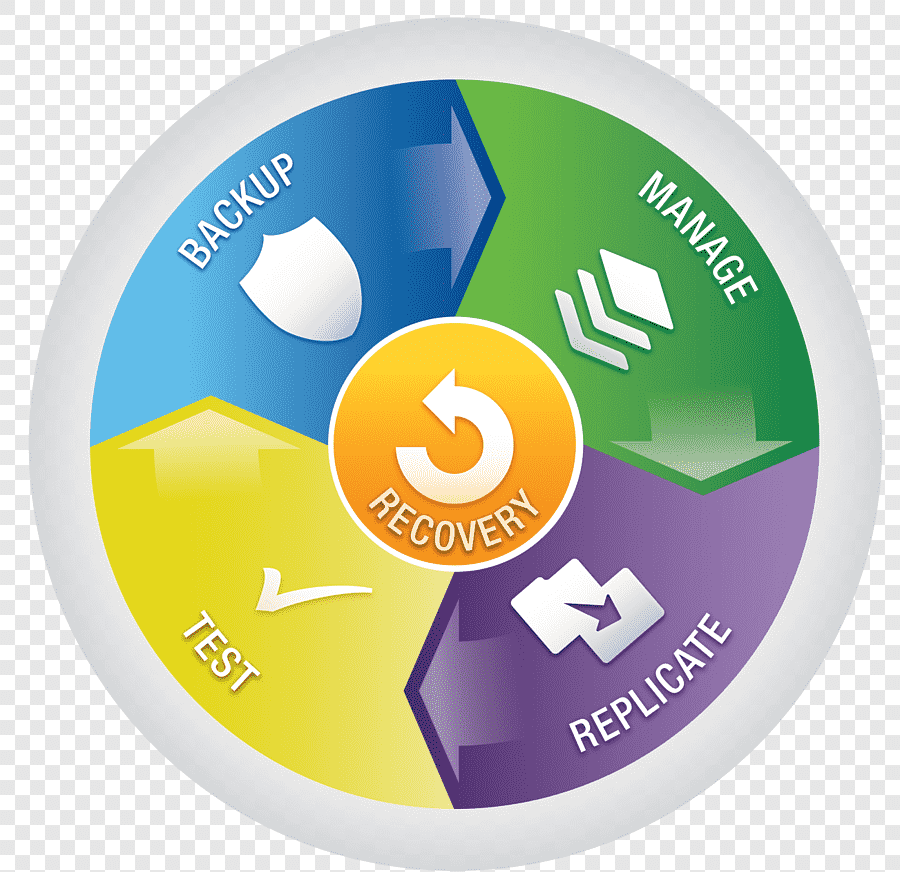
STRATEGY AND PLAN DEVELOPMENT

What is Strategy and Plan Development ?
Business Continuity (BC) Strategy and Plan Development refers to the process of creating a roadmap for ensuring an organization’s critical functions can continue operating even after a cyberattack or other disruptive event. It involves a proactive approach to minimize downtime, data loss, and financial impact while ensuring a swift recovery.
Benefits of Strategy and Plan Development?
- Reduced Downtime and Data Loss: A well-defined BC strategy helps minimize downtime and data loss during a cyberattack or disruption. This translates to reduced financial losses and reputational damage.
- Improved Recovery Time: Having a plan in place allows for a faster and more efficient recovery process, ensuring critical functions are restored quickly.
- Enhanced Decision-Making: The process of analyzing risks and formulating a strategy leads to better decision-making regarding cybersecurity investments and resource allocation.
- Increased Confidence and Resilience: A strong BC strategy fosters confidence within the organization’s leadership and employees, knowing they are prepared to handle disruptions effectively.
- Compliance with Regulations: Many industries have regulations that require organizations to have a BC plan in place.

Benefits Of Strategy and Plan Development?
- Clarity and focus: A well-defined strategy provides a clear understanding of your goals and helps you prioritize tasks and decisions aligned with them.
- Increased motivation and direction: Knowing what you are working towards can be incredibly motivating and provide a sense of purpose.
- Improved decision-making: Having a plan makes it easier to evaluate options and make informed choices based on your long-term objectives.
- Enhanced resource allocation: By understanding your priorities, you can allocate your time, energy, and resources more effectively.
- Greater adaptability: A flexible plan allows you to adjust to changing circumstances and unexpected challenges without losing sight of your overall goals.
- Boosted confidence: Knowing you have a well-thought-out approach can increase confidence in your ability to achieve your goals.
Our Approach
1. Preparation:
- Assemble a Team: Create a dedicated team with representatives from IT, cybersecurity, operations, and management. This team will oversee the entire BC planning process.
- Stakeholder Engagement: Engage key stakeholders across the organization to gain leadership buy-in, understand critical business functions, and ensure everyone is aware of their roles during a disruption.
- Inventory and Classification: Identify all critical business functions, systems, and data within the organization. Classify them based on their criticality and acceptable downtime (RTO) and data loss (RPO).
2. Risk Assessment and Business Impact Analysis (BIA):
- Threat Landscape Analysis: Identify and assess cybersecurity threats your organization faces, including common cyberattacks, phishing attempts, social engineering, malware infections, ransomware attacks, and physical security threats.
- Vulnerability Assessment: Identify vulnerabilities in your IT infrastructure, systems, and applications. This could involve penetration testing, vulnerability scanning, and security audits.
- Impact Analysis: Analyze the potential impact of identified threats on your critical business functions. Consider factors like financial losses, reputational damage, legal ramifications, and operational disruptions for different downtime durations.
3. Strategy Formulation:
- Define Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO): Establish acceptable downtime (RTO) for each critical function and the maximum tolerable data loss (RPO) before recovery is necessary.
- Develop Business Continuity Controls: Implement preventative measures and strategies to minimize the impact of cyberattacks. This could involve:
- Data Backups: Regularly back up critical data with secure offsite storage and frequent testing of backup restoration procedures.
- System Redundancy: Implement redundant systems or cloud-based solutions for critical functions to ensure continued operation if one system fails.
- Disaster Recovery Plan: Develop a plan for restoring critical systems and data in case of a major disaster or cyberattack.
- Patch Management: Implement a system for timely patching of vulnerabilities in software and operating systems.
- Cybersecurity Awareness Training: Train employees on cybersecurity best practices to identify and avoid phishing attempts and social engineering tactics.
- Access Controls: Implement strong access controls to restrict access to sensitive data and systems.
- Cybersecurity Insurance: Consider cyber insurance to help offset financial losses associated with cyberattacks.
4. Business Continuity Plan (BCP) Development:
- Incident Response Plan: Develop a plan outlining the steps to take upon detecting a security incident. This includes containment, eradication, and recovery procedures, assigning roles and responsibilities for different teams.
- Communication Plan: Develop a clear communication plan to ensure timely and consistent communication throughout the organization during a disruption. Define who communicates what information to whom and through which channels.
- Testing and Training: The BCP should be regularly tested through simulations and exercises to identify gaps and ensure its effectiveness. Employees should also be trained on their roles and responsibilities during a cyberattack or other disruptive event.
5. Maintenance and Improvement:
- Regular Review and Updates: Regularly review and update the BC strategy and plan to reflect changes in the organization's business landscape, evolving threats, and advancements in technology.
- Lessons Learned: After a real-world incident or a BC plan test, conduct a thorough review to identify areas for improvement and update the plan accordingly.
- Continuous Improvement: Business continuity planning is an ongoing process that needs to be adapted and improved based on new information, threats, and best practices.