DATA PROTECTION IMPACT ASSESSMENT

What is Data Protection Impact Assessment?
A Data Protection Impact Assessment (DPIA) is a process designed to help you identify and minimize the risks to personal data associated with a project or activity. It’s particularly important for situations where processing personal data poses a high risk to individuals’ rights and freedoms.
Benefits of Data Protection Impact Assessment?
- Compliance: DPIAs demonstrate proactive compliance with data protection regulations like GDPR, CCPA, and others, reducing the risk of fines and penalties.
- Risk Mitigation: Identifying and evaluating risks early on allows for the implementation of appropriate safeguards and mitigations, preventing data breaches and protecting individuals’ privacy.
- Improved Data Management: DPIAs encourage organizations to optimize data collection and processing practices, reducing data storage and usage costs.
- Enhanced Transparency and Trust: Conducting and sharing DPIAs demonstrates transparency and accountability regarding data protection practices, building trust with stakeholders and customers.
- Informed Decision-Making: DPIAs offer a comprehensive analysis of data processing activities, enabling informed decisions about data usage and minimizing legal and reputational risks.
- Reduced Operational Costs: Early identification and mitigation of risks can prevent costly data breaches and legal challenges, saving money in the long run.


Benefits Of Data Protection Impact Assessment?
- Compliance: DPIAs demonstrate proactive compliance with data protection regulations like GDPR, CCPA, and others, reducing the risk of fines and penalties.
- Risk Mitigation: Identifying and evaluating risks early on allows for the implementation of appropriate safeguards and mitigations, preventing data breaches and protecting individuals’ privacy.
- Improved Data Management: DPIAs encourage organizations to optimize data collection and processing practices, reducing data storage and usage costs.
- Enhanced Transparency and Trust: Conducting and sharing DPIAs demonstrates transparency and accountability regarding data protection practices, building trust with stakeholders and customers.
- Informed Decision-Making: DPIAs offer a comprehensive analysis of data processing activities, enabling informed decisions about data usage and minimizing legal and reputational risks.
- Reduced Operational Costs: Early identification and mitigation of risks can prevent costly data breaches and legal challenges, saving money in the long run.
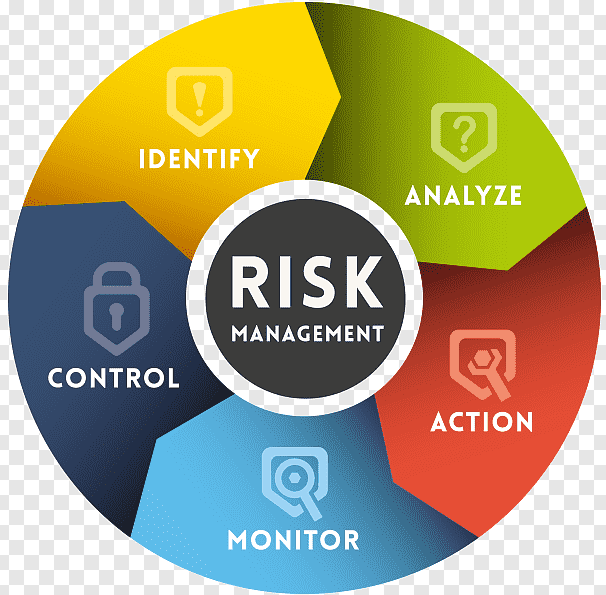
Our Approach
1. Identifying the Need for a DPIA:
The first step is to determine if your processing activities require a DPIA. This involves considering factors like:
- Type of Data Processed: Processing special categories of data (e.g., health information, PII, sensitive info etc.) or large-scale data processing typically necessitates a DPIA.
- Data Subjects at Risk: Processing data that could significantly impact individual's or organizations sensitive information triggers a DPIA requirement.
- Innovative Technologies: Using new technologies with inherent privacy risks, often requires a DPIA.
2. Describing the Processing Activities:
Clearly defining the data processing activities under assessment. This includes:
- What personal data is collected and processed.
- The purposes and legal basis for processing.
- The data subjects involved.
- The technical and organizational measures in place.
3. Consulting with Relevant Stakeholders:
Engaging with internal and external stakeholders affected by the processing, including:
- Data protection officer (DPO) if you have one.
- Individuals whose data is processed.
- IT and security teams.
- Relevant departments based on the processing activity.
4. Assessing the Risks to Individuals:
Evaluating the potential negative impacts on individuals' rights and freedoms, considering:
- Confidentiality: Can data be accessed by unauthorized individuals?
- Integrity: Can data be altered or manipulated?
- Availability: Can individuals access their data upon request?
- Non-Discrimination: Does the processing lead to unfair treatment?
- Other Rights: Consider impacts on specific rights like freedom of expression and data portability.
5. Identifying and Assessing Mitigation Measures:
Based on the identified risks, we shall determine appropriate measures to minimize them. This could involve:
- Implementing technical controls (e.g., encryption, access control).
- Adopting organizational measures (e.g., data minimization, staff training).
- Seeking alternative processing methods with lower risks.
6. Documenting the DPIA:
Creating a comprehensive report and documenting the DPIA process and its outcomes. This includes:
- The rationale for conducting the DPIA.
- The description of processing activities.
- The identified risks and their severity.
- The implemented mitigation measures.
- The conclusion on whether the processing is acceptable based on the risks and measures.