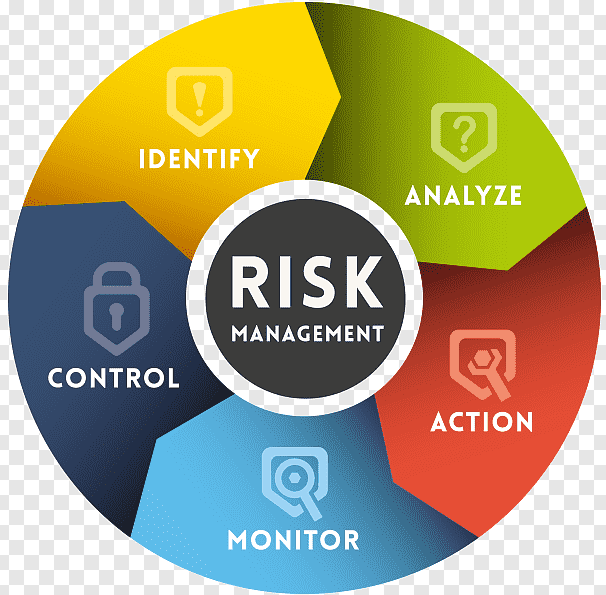
INFOSEC ARCHITECTURE AND STRATEGY DEVELOPMENT
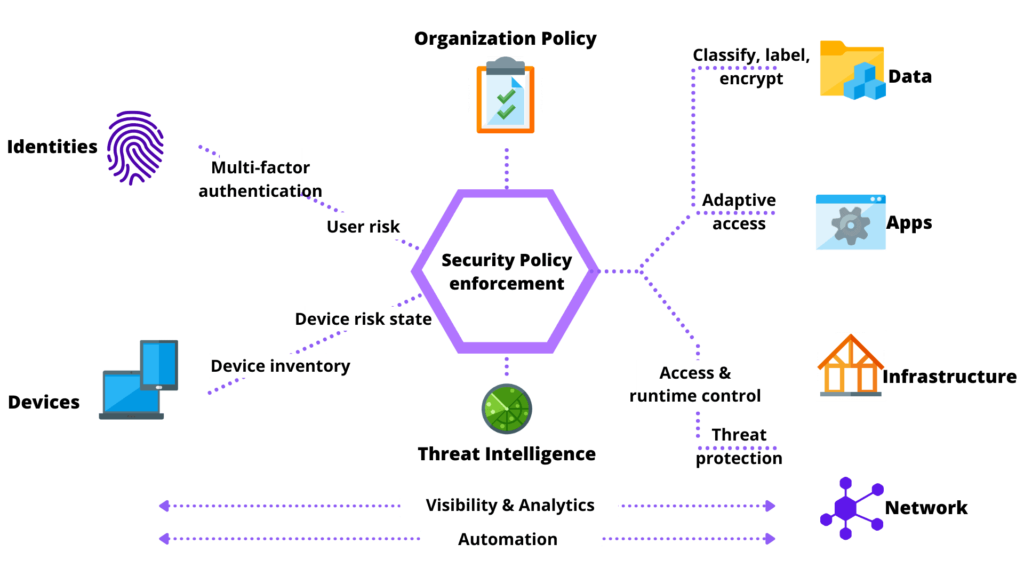
What is Infosec Architecture and Strategy Development?
Infosec Architecture and Strategy Development are two interconnected elements that form the foundation of your organization’s cybersecurity posture.
Benefits of Infosec Architecture and Strategy Development?
- Reduced Risk: By identifying and prioritizing vulnerabilities, the architecture acts as a roadmap for implementing effective security controls, minimizing the attack surface and reducing the risk of breaches.
- Proactive Approach: Strategy development emphasizes prevention over reaction, allowing you to anticipate threats and proactively implement countermeasures instead of scrambling to respond to incidents.
- Compliance Adherence: Alignment with regulations and industry standards simplifies compliance processes and reduces the risk of fines or penalties.
- Optimized Resource Allocation: Prioritization ensures resources are directed towards the most critical security needs, avoiding wasteful spending on ineffective measures.
- Standardized Solutions: Consistent policies and procedures across the organization streamline security management and reduce operational costs.
- Simplified Operations: An established architecture ensures everyone’s on the same page, facilitating collaboration and improving overall security efficiency.
- Adaptability to Change: The architecture should be flexible to accommodate new technologies, business processes, and evolving threats, ensuring your security adapts to changing needs.

Benefits of Infosec Architecture and Strategy Development?
- Reduced Risk: By identifying and prioritizing vulnerabilities, the architecture acts as a roadmap for implementing effective security controls, minimizing the attack surface and reducing the risk of breaches.
- Proactive Approach: Strategy development emphasizes prevention over reaction, allowing you to anticipate threats and proactively implement countermeasures instead of scrambling to respond to incidents.
- Compliance Adherence: Alignment with regulations and industry standards simplifies compliance processes and reduces the risk of fines or penalties.
- Optimized Resource Allocation: Prioritization ensures resources are directed towards the most critical security needs, avoiding wasteful spending on ineffective measures.
- Standardized Solutions: Consistent policies and procedures across the organization streamline security management and reduce operational costs.
- Simplified Operations: An established architecture ensures everyone’s on the same page, facilitating collaboration and improving overall security efficiency.
- Adaptability to Change: The architecture should be flexible to accommodate new technologies, business processes, and evolving threats, ensuring your security adapts to changing needs.
Our Approach
1. Assessment and Goal Setting:
- Current State Assessment: Evaluating your current security posture, identifying vulnerabilities, strengths, and weaknesses in infrastructure, policies, and processes.
- Business Alignment: Understanding your organization's overall goals, risk tolerance, and compliance requirements.
- Security Goals Definition: Defining clear security goals aligned with business objectives, focusing on confidentiality, integrity, and availability of information.
2. Information Asset Identification and Classification:
- Identifying and Inventorying all Assets: This includes data, applications, systems, devices, and networks.
- Classification: Categorizing identified assets based on their value, sensitivity, and criticality to prioritize security measures.
3. Threat Identification and Risk Assessment:
- Identifying Potential Threats: Analyzing internal and external threats relevant to your industry and size.
- Risk Assessment: Evaluating the likelihood and impact of potential threats on your identified assets. This helps prioritize risks and inform your security strategy.
4. Architecture Design and Development:
- Defining Security Controls: Choosing appropriate controls (technical, administrative, and physical) to address identified risks and protect classified assets.
- Architecture Definition: Designing the security architecture, including network segmentation, access control, encryption, etc. Considering cloud security, mobile security, and data security controls as needed.
- Standards and Frameworks: Aligning your architecture with relevant security standards and frameworks like NIST Cybersecurity Framework or ISO 27001.
5. Strategy Implementation and Policy Development:
- Developing Security Policies and Procedures: These documents translate your security strategy into actionable steps for employees and other stakeholders.
- Implementation Roadmap: Creating a phased implementation plan with defined timelines and resource allocation.
- Change Management: Addressing potential resistance to change through user training, communication, and awareness programs.
6. Ongoing Monitoring, Testing, and Improvement:
- Regularly Monitoring: Continuously monitoring security controls and assessing their effectiveness.
- Vulnerability Assessments and Penetration Testing: Identifying and addressing new vulnerabilities.
- Incident Response Preparedness: Ensuring your organization is prepared to respond to security incidents effectively.
- Metrics and Reporting: Tracking key metrics to measure security performance and inform continuous improvement.