vCISA - VIRTUAL CISA

What is vCISA – Virtual CISA?
vCISA, or Virtual Certified Information Systems Auditor, is a professional designation acknowledging proficiency in auditing information systems.
A vCISA has comprehensive understanding of auditing principles and practices. vCISA has competence in assessing, evaluating, and ensuring the security and effectiveness of information systems. vCISA’s are equipped to navigate the complexities of modern information technology environments with confidence and expertise.
Benefits of vCISA – Virtual CISA?
Virtual Information Systems Auditing: Conducting audits of information systems in virtual environments to assess their security, effectiveness, and compliance with regulatory standards and industry best practices.
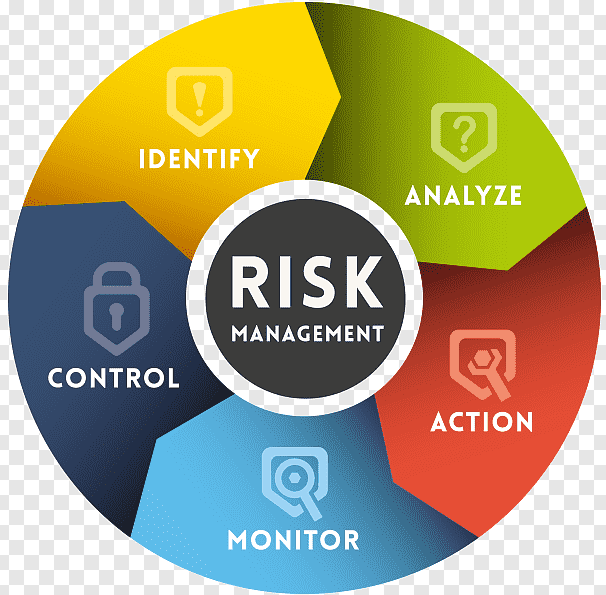
Risk Assessment and Management: Identifying, evaluating, and mitigating potential risks associated with information systems in virtual settings, helping organizations to protect their data and assets.
Virtual Compliance Audits: Ensuring that information systems adhere to relevant regulations, standards, and policies, even in virtual or remote work environments.
Security Consulting: Providing expert guidance and recommendations to improve the security posture of virtual information systems, including network security, data protection, and access control.
Training and Education: Offering virtual training programs, workshops, and seminars to educate organizations and professionals on information systems auditing principles and practices.
Virtual Incident Response: Assisting organizations in responding to cybersecurity incidents and breaches occurring in virtual environments, including incident investigation, containment, and recovery.


Benefits of vCISA – Virtual CISA?
Virtual Information Systems Auditing: Conducting audits of information systems in virtual environments to assess their security, effectiveness, and compliance with regulatory standards and industry best practices.
Risk Assessment and Management: Identifying, evaluating, and mitigating potential risks associated with information systems in virtual settings, helping organizations to protect their data and assets.
Virtual Compliance Audits: Ensuring that information systems adhere to relevant regulations, standards, and policies, even in virtual or remote work environments.
Security Consulting: Providing expert guidance and recommendations to improve the security posture of virtual information systems, including network security, data protection, and access control.
Training and Education: Offering virtual training programs, workshops, and seminars to educate organizations and professionals on information systems auditing principles and practices.
Virtual Incident Response: Assisting organizations in responding to cybersecurity incidents and breaches occurring in virtual environments, including incident investigation, containment, and recovery.
Our Approach
1. Client Consultation:
- Understanding your needs, objectives, and specific requirements related to information systems auditing in virtual environments.
2. Assessment and Planning:
- A comprehensive assessment is conducted to evaluate your existing information systems, identifying potential risks and vulnerabilities, and determining the scope of the audit or services required.
- Based on this assessment, a detailed plan is developed outlining the approach, methodologies, and timeline for the engagement.
3. Execution:
- Carrying out the agreed-upon services, which may include conducting virtual audits, risk assessments, compliance checks, or security evaluations of your information systems.
- This phase involves thorough analysis, documentation, and reporting of findings.
4. Recommendations and Remediation:
- Upon completion of the assessment or audit, comprehensive reports detailing findings, recommendations, and actionable insights to address identified risks and improve the security and effectiveness of your information systems shall be provided.
5. Follow-Up and Support:
- Offering ongoing support and guidance to you in implementing recommended solutions, addressing any concerns or questions, and ensuring continued compliance and security in your environments.