VMaaS - VULNERABILITY MANAGEMENT AS A SERVICE

What is VMaaS – Vulnerability Management as a Service?
VMaaS, or Vulnerability Management as a Service, manages the ongoing process of identifying, assessing, prioritizing, and remediating vulnerabilities across your IT infrastructure and applications.
Benefits of VMaaS – Vulnerability Management as a Service ?
Improved Efficiency and Automation:
- Continuous Scanning: VMaaS providers typically offer automated and continuous scanning of your IT infrastructure, including systems, applications, and cloud environments. This eliminates the need for manual scans and ensures vulnerabilities are identified quickly.
- Prioritization and Remediation: VMaaS solutions prioritize vulnerabilities based on severity, exploitability, and potential impact, allowing you to focus on the most critical issues first. Additionally, some providers offer automated patching or provide guidance for efficient remediation.
Enhanced Expertise and Resources:
- Access to Security Experts: VMaaS providers have security professionals on staff who can help you understand complex vulnerabilities, recommend remediation strategies, and stay up-to-date on the latest threats.
- Advanced Tools and Technologies: VMaaS providers leverage advanced vulnerability scanning tools and threat intelligence platforms that may not be readily available or affordable for smaller organizations.

VMaaS – Vulnerability Management as a Service ?
Improved Efficiency and Automation:
- Continuous scanning: VMaaS providers typically offer automated and continuous scanning of your IT infrastructure, including systems, applications, and cloud environments. This eliminates the need for manual scans and ensures vulnerabilities are identified quickly.
- Prioritization and remediation: VMaaS solutions prioritize vulnerabilities based on severity, exploitability, and potential impact, allowing you to focus on the most critical issues first. Additionally, some providers offer automated patching or provide guidance for efficient remediation.
Enhanced Expertise and Resources:
- Access to security experts: VMaaS providers have security professionals on staff who can help you understand complex vulnerabilities, recommend remediation strategies, and stay up-to-date on the latest threats.
- Advanced tools and technologies: VMaaS providers leverage advanced vulnerability scanning tools and threat intelligence platforms that may not be readily available or affordable for smaller organizations.
Our Approach
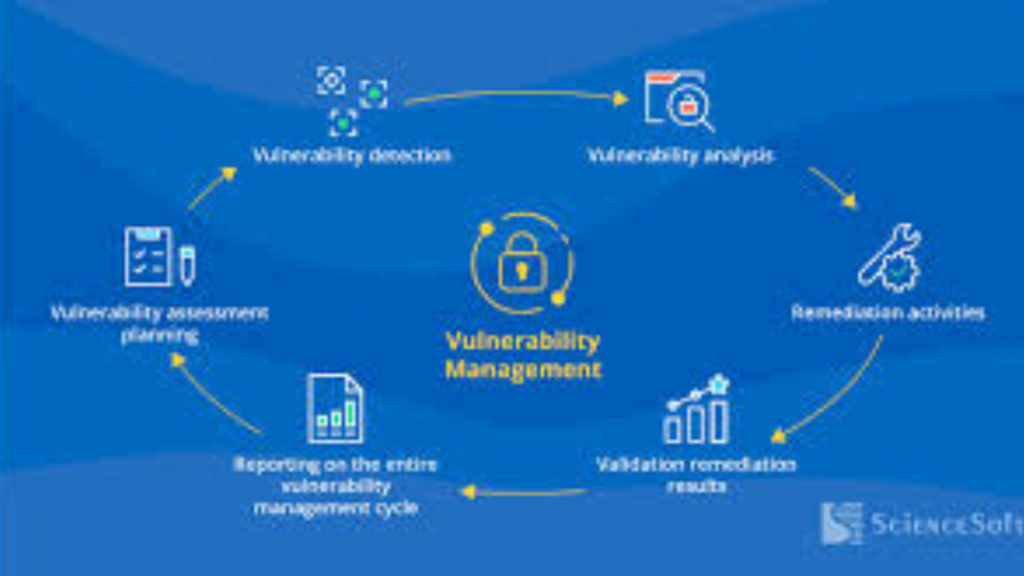
1. Discovering and Inventorying :
- Continuously scanning your systems (internal and external) to identify all assets, including devices, applications, and configurations.
- This creates a comprehensive inventory, helping us understand your attack surface and potential vulnerabilities.
2. Vulnerability Assessment and Scanning:
- Using vulnerability scanners to identify known weaknesses in your identified assets.
- These scanners compare your systems to databases of known vulnerabilities and exploit techniques.
- Reports are generated, detailing the vulnerabilities found, their severity, and potential impact.
3. Prioritization and Risk Analysis:
- Not all vulnerabilities are created equal. We prioritize findings based on various factors:
- Severity: How easily exploitable is the vulnerability?
- Impact: What damage could occur if exploited?
- Business criticality: How important is the affected asset to your operations?
- This prioritization helps us focus on addressing the most critical vulnerabilities first.
4. Reporting and Remediation:
- Providing detailed reports summarizing discovered vulnerabilities, their severity, and recommended remediation actions.
- Providing guidance on available patches and mitigation strategies.
- Establishing clear remediation plans to address identified vulnerabilities promptly and effectively.
5. Continuous Monitoring and Updates:
- VMaaS is a cyclical process, not a one-time fix. New vulnerabilities are discovered regularly, and your IT environment constantly evolves.
- Continuous monitoring ensures you stay up-to-date on new threats and promptly address emerging vulnerabilities, hence keeping your environment secure.